Lets learn the realm of data recovery
4
English | Hindi | Spanish | French
Multi Language Training
9000+
trainee
worldwide
10000+
Data Recovery Case
Assistance yearly
3000+
Remote assistance
yearly
10+
years in data recovery
service and training
100%
DATA
SECURITY & PRIVACY
Professional Online Data Recovery Training
We have courses specially designed for students and professionals who want to pursue a career in the field of data recovery. The courses are developed by experienced industry professionals and offer in-depth knowledge, which is industry-relevant. Recover your investment by just completing one data recovery task.
Users can access our course materials online and study according to their convenience. They get Lifetime access and updates and useful notes along with technical assistance that help them in shaping a better career.
Our Online Data Recovery Training Solutions
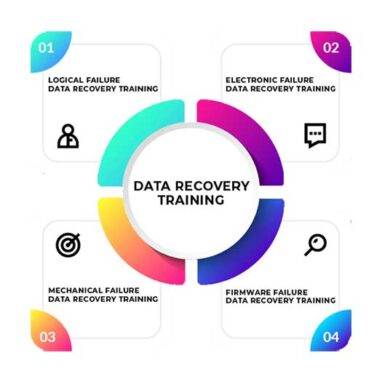
Data Recovery and Hard Disk Repair
The Data recovery training course at Data Empires is designed to give learners…
Read More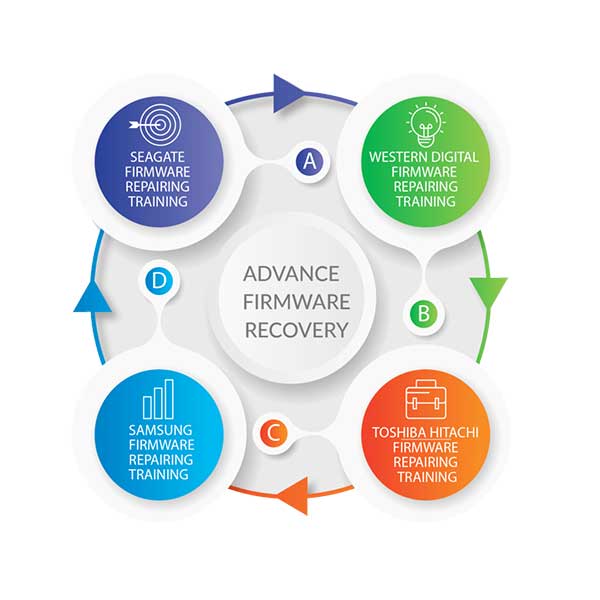
Advance Hard Drive Firmware Repairing
Every data recovery specialist should have the knowledge, skills, and…
READ MORE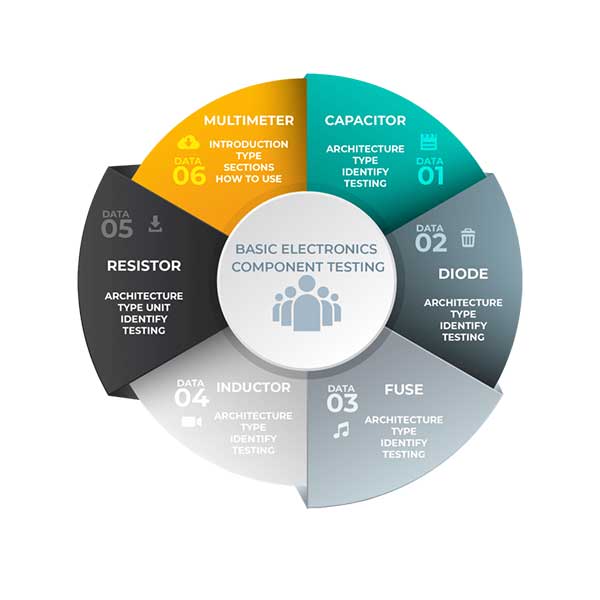
Basic Electronics And Component Testing
The PCB or Printed circuit board is an essential component of most…
READ MOREWhy should I have to learn data recovery?
Our Package
USD 50.00
Professional
- Lifetime web portal access?
- Logical failure data recovery training
- Mechanical Failure data recovery training
- Electrical (PCB) failure data recovery training
- Basic information and logical values
- Hard disk firmware basic information
- Seagate Firmware Repairing Software
- Wd firmware failure data recovery training
- Basic electronics and component testing
- Data recovery solutions case study
- Expert data recovery solutions
- Advance firmware repairing training introduction on MRT tool
- MRT seagate firmware repairing training
- MRT WD firmware repairing training
- Unlimited resource download
- One time pay, Lifetime update
- Access any time and many times. No restrictions.
- All upcoming course video access